In the realm of modern application development, especially when exposing APIs such as Microsoft Dataverse to external clients, service accounts play a crucial role. These dedicated accounts are designed to handle automated, app-to-app interactions, rather than for user-driven tasks. By using service accounts, organizations can bolster security, streamline maintenance, and ensure better control over resource access. In this article, we’ll examine why you should use a service account for your external integrations and how it optimizes both security and maintenance for your apps.
Why Use a Service Account?
Service accounts play a crucial role in enhancing security, managing permissions, and ensuring smooth automation for applications and services. Below are key reasons why service accounts are essential for your infrastructure :
- 🔐Dedicated Credentials: Service accounts offer a specific username and password (or other authentication tokens) that belong to an application, not a human. This keeps user credentials isolated from automated processes, reducing the risk of unauthorized access if an individual user’s account is compromised.
- ⚙️Streamlined Permissions: By setting the right permissions and roles on a service account, you can grant external apps exactly the access they need—no more, no less. This principle of least privilege helps minimize security risks and prevents accidental data exposure.
- 📊Auditing and Compliance: When a service account is used to call APIs or perform tasks, its actions are logged under that specific account. This makes it easier to track and audit changes, ensuring compliance with regulatory standards.
- 🔄Easier Maintenance: Isolating automated processes to a service account allows you to manage passwords, tokens, and access policies without impacting human users. This streamlined approach simplifies updates, rotations, and deactivations if necessary.
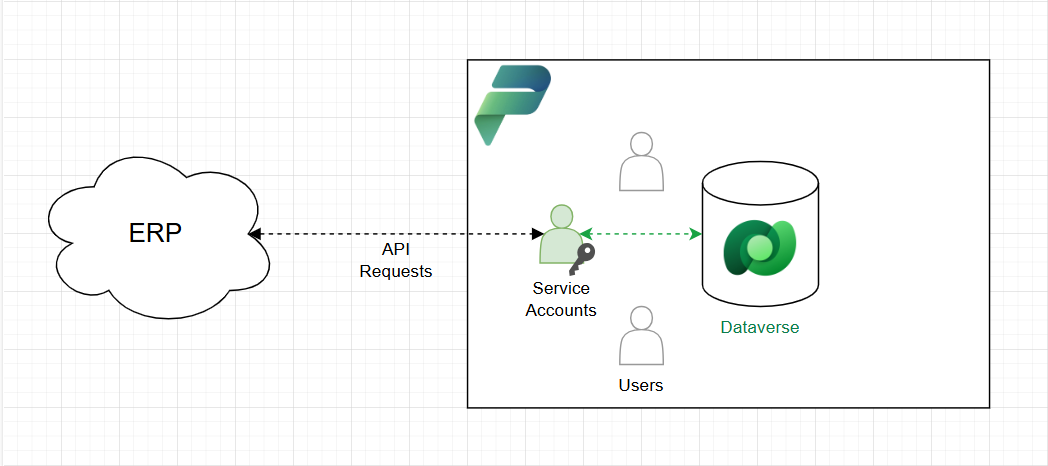
Let’s consider the diagram above. In this scenario, the ERP contains stock information. To update the CRM with the current stock status, the ERP uses a service account, which can be named "erp-service-account".
This allows us to track all records created by the service account and assign it a security role to restrict its capabilities to specific tables, ensuring it can only manipulate the data necessary for its function. With the Power Platform features, you will even be able to impersonnate the creation with another user.
Key Advantages for Dataverse Exposed APIs
Using a service account to expose Dataverse APIs to external applications offers several critical advantages. It provides better control over integrations by precisely managing what data and functions are accessible, ensuring that external applications operate within their intended scope. This reduces the risk of unauthorized access or overreach. Additionally, service accounts help in minimizing human error—unlike user-driven credentials that can be lost, improperly shared, or leaked, service accounts use tokens and credentials strictly for application purposes, mitigating these vulnerabilities. As your application ecosystem expands, scalability improves through service accounts, allowing seamless management of new connections and microservices without overburdening individual user accounts or risking exposure of personal credentials. Furthermore, service accounts enhance monitoring and logging, enabling more accurate tracking of API calls and making it easier to detect unusual activity or spikes in usage. This layered approach to security and efficiency strengthens overall governance and ensures smoother, more reliable integrations with Dataverse.
How to create a service account
Creating a service account in Dynamics 365 involves setting up a non-human user with specific rights to perform automated operations, such as executing workflows, integrating with third-party applications, or making API calls. Here are the main steps to create and configure a service account:
Step 1: Create a User in Azure Active Directory (AAD)
- Access Azure Active Directory via the Azure portal.
- In Users, click New User.
- Fill in the necessary information (name, username, etc.).
- Set a temporary password that will be changed on first login.
- Save the user.
Step 2: Edit User Settings
- Find and select the service account you want to configure.
- Once in the user's profile, click Properties.
- Scroll down to the Password section. password.
- Enable the Password never expires option.
- Click Save to apply the changes.
Step 3: Assign a License to the User
- Still in the Azure portal, select the user you created.
- Click Licenses > Assign Licenses.
- Select a Dynamics 365 Customer Engagement license (or the appropriate license depending on your environment).
- Validate to apply the license.
Step 4: Add the User to Dynamics 365
- Go to Dynamics 365 (Administration Center) Power Platform).
- Select the target environment and click Settings > Users & Permissions > Users.
- Click New and add the Azure AD user you created earlier.
Step 5: Assign a License to the User
- In Dynamics 365, go to Settings > Security > Users.
- Find the added service account.
- Click Manage Roles and assign the necessary roles (for example, System Administrator or Custom Service Role).
- Create a custom role with specific rights if necessary to limit access to what is strictly necessary (principle of least privilege).
Step 6: Configure Authentication (if required)
- If the service account is used for API calls or integrations, set up an app registration in Azure AD and assign the service user.
- Enable OAuth2 authentication and generate a client secret for programmatic access.
Best Practices for Service Accounts
1. Use Strong Authentication Methods: Where possible, use Multi-Factor Authentication (MFA) or token-based credentials to protect against unauthorized logins.
2. Apply the Principle of Least Privilege: Grant the minimum permissions necessary for the service account to perform its tasks. Avoid giving administrative privileges unless absolutely needed.
3. Rotate Credentials Regularly: Update passwords or tokens periodically and whenever there is a security event. Regular rotation lowers the potential impact of stolen credentials.
4. Audit and Monitor Logins: Track and log every login or API call made by the service account. Use these logs for ongoing audits and compliance checks.
5. Segregate Duties: If multiple services or apps need access to Dataverse, create separate service accounts. This prevents one compromised account from affecting unrelated integrations.
Conclusion
Service accounts provide a robust way to secure and manage automated processes, especially when exposing sensitive APIs like Dataverse to external applications. By using dedicated credentials and adhering to best practices, you not only tighten your security posture but also simplify maintenance and troubleshooting. With proper auditing, permission management, and credential rotation, service accounts can help your organization confidently scale its integrations while safeguarding critical data.



 Français
Français English
English